Joker Malware Explained: A Simple Guide to Android’s Persistent Threat
What is Joker Malware?
Joker is a spyware and premium dialer trojan (also known as “Bread”) that disguises itself as legitimate mobile applications on the Google Play Store. The malware primarily focuses on billing fraud and data theft, making it extremely dangerous for Android users.

The malware serves multiple malicious purposes:
Financial Fraud: Joker’s main goal is to secretly subscribe users to premium mobile services without their knowledge or consent, generating revenue for attackers through toll fraud.
Data Theft: The malware steals sensitive information including SMS messages, contact lists, device information, and intercepts one-time passwords (OTPs) used for two-factor authentication.
Remote Control: Establishes communication with command-and-control (C&C) servers to receive instructions and download additional malicious components.
Step-by-Step Infection Process:
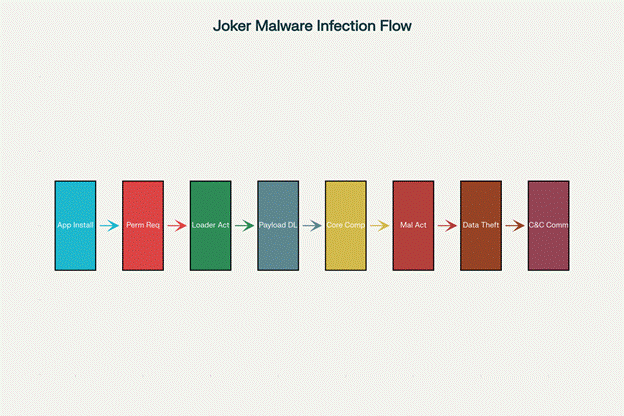
Joker Malware Infection Process: Step-by-Step Execution Flow
App Distribution: Joker spreads through malicious applications disguised as legitimate apps (camera apps, wallpapers, games, messaging apps, health apps) available on the Google Play Store.
Phase 1: Initial Infiltration
Installation: When users download and install the infected app, it appears to function normally while hiding its malicious components.
Phase 2: Permission Acquisition
Permission Requests: The malware requests seemingly normal permissions that enable its malicious activities:
- READ_PHONE_STATE (to access device information)
- BIND_NOTIFICATION_LISTENER_SERVICE (to intercept notifications and OTPs)
- CHANGE_WIFI_STATE (to force cellular connection for billing fraud)
- SMS permissions (to read and send text messages)
Phase 3: Loader Stage Activation:
Splash Screen Deception: The app displays a normal splash screen while silently performing initialization processes in the background.
Configuration Download: The loader downloads an obfuscated and AES-encrypted configuration containing information about the second stage payload.
Phase 4: Payload Deployment:
Multi-Stage Loading: Modern Joker variants use sophisticated multi-stage payload deployment:
First Stage: Downloads initial payload from C&C server
Second Stage: Downloads additional components for specific malicious activities
Third Stage: Contains the actual billing fraud code and data theft modules
Dynamic Code Loading: The malware uses techniques like Base64 encoding and DEX file obfuscation to hide malicious code from security scanners.
Phase 5: Malicious Activity Execution
Premium Service Subscription: The core malicious activity involves:
1. Opening URLs to advertising websites with premium service offers
2. Automatically clicking on subscription buttons
3. Waiting for SMS confirmation codes
4. Extracting OTP codes from intercepted messages
5. Completing the subscription process without user knowledge.
Data Exfiltration: Simultaneously steals and transmits user data including:
- Contact lists (sent to C&C in encrypted format)
- SMS messages and notifications
- Device information and screenshots
- Location data and timestamps.
Phase 6: Stealth Operations:
SMS Suppression: Hides subscription confirmation messages from users to avoid detection.
Background Operations: Runs silently in the background with minimal system footprint
Anti-Detection: Uses various evasion techniques including:
- Code obfuscation with tools like BlackObfuscator
- Native libraries written in Rust or Go
- Encrypted payloads stored in app assets
- GitHub repositories to host malicious components.
Phase 7: Command and Control Communication:
C&C Registration: The malware registers the infected device with remote command-and-control servers.
Job Execution: Periodically requests new commands from C&C servers and executes them in strict order.
Progress Reporting: Sends completion notifications back to C&C servers after successful operations.
Advanced Evasion Techniques:
Joker employs sophisticated methods to bypass security measures:
Manifest File Manipulation: Hides malicious DEX files as Base64 encoded strings within AndroidManifest.xml files.
Geographic Targeting: Checks SIM information to target specific countries and mobile operators.
Versioning Strategy: Uploads clean app versions initially, then adds malicious code through updates.
Flutter Framework Abuse: Uses legitimate Google development frameworks to make malicious code appear legitimate.
Impact and Scale:
- Joker has had massive global impact:
- Over 1,700 malicious apps removed from Google Play Store as of 2020
- More than 500,000 users affected by individual campaigns
- Millions of downloads across infected applications
- Active in multiple countries including Thailand, Europe, and Asia

